
Mike Schmidt dealing with undisclosed illness – The Mercury

Widespread Exploitation of VMware Workspace ONE Access CVE-20 - vulnerability database
F5 BIG-IP Remote Code Execution Vulnerability (CVE-2020-5902) - vulnerability database
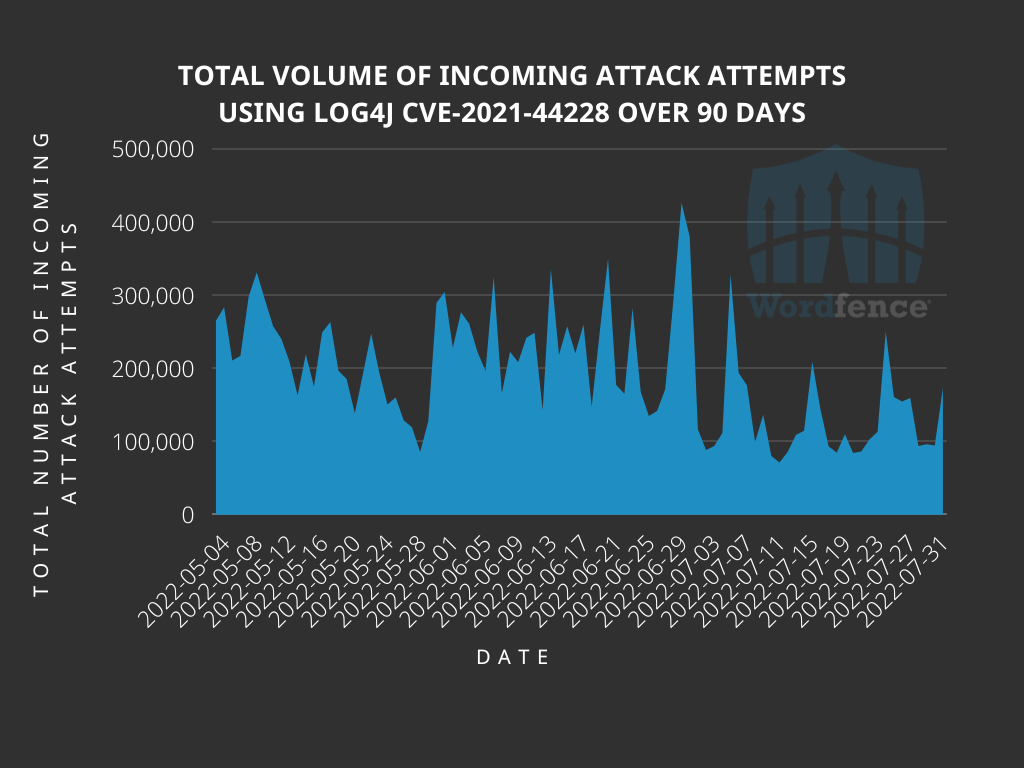
Analyzing Attack Data and Trends Targeting Log4J - vulnerability database
MORE
dm_project/output_2012.json at master · bennettmountain/dm_project · GitHub

NoxPlayer Supply-Chain Attack is Likely the Work of Gelsemiu - vulnerability database
quality/docs/js/camera_ready_nd8_dev_sample100.json at main · nyu-mll/quality · GitHub
quacs-data/faculty.json at master · quacs/quacs-data · GitHub

Microsoft Exchange Server Exchange Control Panel Fixed Crypt - vulnerability database

Exchange, Fortinet Flaws Being Exploited by Iranian APT, CIS - vulnerability database

Mike Schmidt - The Mental Illness Happy Hour

Mike Schmidt - Director of Medical Sales - Elite Executive Partners

KLA12442 RCE vulnerability in LibreOffice - info database
hn-hiring-mapped/src/web/data/2015-06.json at gh-pages · gaganpreet/hn-hiring-mapped · GitHub
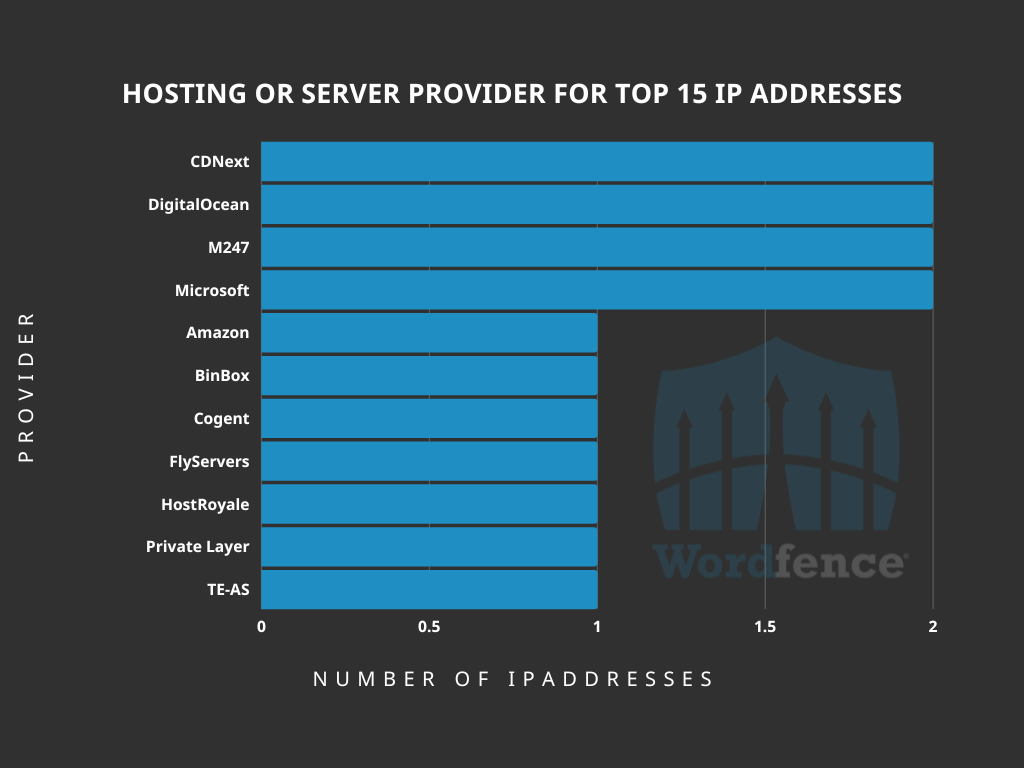
Analyzing Attack Data and Trends Targeting Log4J - vulnerability database














